Disable Aslr Windows 10
If you don't want a system-wide change, use ADDRNORANDOMIZE personality to temporarily disable ASLR. Iskysoft dvd creator for windows. Controlling this personality flag can be done with setarch and its -R option ( manpage ), prepending a command. Oct 13, 2017 ASLR at work. Windows 10 applies ASLR holistically across the system and increases the level of entropy many times compared with previous versions of Windows to combat sophisticated attacks such as heap spraying. https://golnh.netlify.app/wordpress-theme-for-download-site.html. 64-bit system and application processes can take advantage of a vastly increased memory space, which makes it even more difficult for malware to predict where Windows 10. In Windows 10, ASLR works just fine on programs that have opted in. That includes Office 2013 and Office 2016, every program in the Adobe Creative Cloud suite, modern browsers like Chrome and Firefox, every executable included with Windows itself, and every program distributed through the Windows Store.
-->Specifies whether to generate an executable image that can be randomly rebased at load time by using the address space layout randomization (ASLR) feature of Windows that was first available in Windows Vista.
Syntax
/DYNAMICBASE[:NO]
Remarks
The /DYNAMICBASE option modifies the header of an executable image, a .dll or .exe file, to indicate whether the application should be randomly rebased at load time, and enables virtual address allocation randomization, which affects the virtual memory location of heaps, stacks, and other operating system allocations. The /DYNAMICBASE option applies to both 32-bit and 64-bit images. ASLR is supported on Windows Vista and later operating systems. The option is ignored by earlier operating systems.
By default, /DYNAMICBASE is enabled. To disable this option, use /DYNAMICBASE:NO. The /DYNAMICBASE option is required for the /HIGHENTROPYVA option to have an effect.
To set this linker option in Visual Studio
Open the project Property Pages dialog box. For more information, see Set C++ compiler and build properties in Visual Studio.
Select the Configuration Properties > Linker > Advanced property page.
Modify the Randomized Base Address property.
To set this linker option programmatically
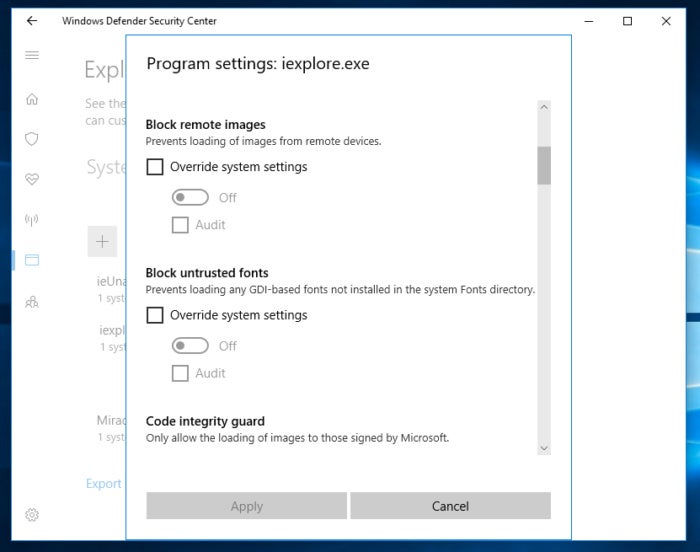
- See RandomizedBaseAddress.
See also

Here is the scenario - You have a legacy application where you wish to load a DLL or module at a fixed or preferred base address. Why would you need it?, that is because in the EXE or DLL code you may make use of the absolute addresses and pointers. This application would work great on Windows XP or older OS, but on Windows Vista you would see that your DLL fails to load at preferred address as some other module is already loaded in the asked virtual address space range. You would notice that all the dlls including system dlls and custom dlls would be loaded at random addresses.
Here is why it happens:
Starting from Windows Vista a new security feature is added called Address Space Layout Randomization (ASLR) which will randomize all (system + user) Loaded DLLs. You may find more information at MSDN: Windows Vista ISV Security .
In any version of Windows OS there is *no* guarantee that a process or DLL will always load at same address space or it will get a particular /FIXED (Fixed Base Address). You may specify a preferred base address using /BASE (Base Address) linker option and in case “preferred” base address in not available your application must be adaptive to the rebasing/relocation of the image or DLL.
Ideally we should never make this assumption or requirement that a DLL will not be relocated. We must not rely on where the process or DLL is loaded.
DLL relocation may happen when 'almost anything' changes, including the installation of service packs, QFEs, third party products, and other major versions of Windows.
Out of curiosity, you may have a question:
1. Is there any way to disable ASLR ?
Unfortunately there is no legitimate way to disable ASLR on Windows Vista and later. In fact, it is a security enhancement and no one should try disabling it.
2. What is the memory address space range in virtual memory map where system DLLs and user DLLs could load?
I would say, there is as such no specific virtual address space range, the DLLs can be loaded at any random address.
You may find more information about ASLR at following blog posts:
Early in the boot process, the Memory Manager picks a random DLL image-load bias from one of 256 64KB-aligned addresses in the 16MB region at the top of the user-mode address space. As DLLs that have the new dynamic-relocation flag in their image header load into a process, the Memory Manager packs them into memory starting at the image-load bias address and working its way down.
Executables that have the flag set get a similar treatment, loading at a random 64KB-aligned point within 16MB of the base load address stored in their image header. Further, if a given DLL or executable loads again after being unloaded by all the processes using it, the Memory Manager reselects a random location at which to load it. Figure 7 shows an example address-space layout for a 32-bit Windows Vista system, including the areas from which ASLR picks the image-load bias and executable load address.
Hence, to determine the range is impractical. The only way is to look at all the base addresses for all the system DLLs, and the add 16MB to the highest one and subtract 16MB from the lowest one. Please note that the base address in any of the system DLLs could change with any update so there is no dependable way to get the range.
There is a flag in the EXE header that marks if it will get a random base address (/DYNAMICBASE)
The base address that is chosen will be somewhere in this range: (BaseAddressInExeHeader-16mb) >= NewBaseAddress <= (BaseAddressInExeHeader +16mb)
The moral of the story is – “no virtual address” is guaranteed available and we should not rely that a process or DLL will be loaded at same address space or at preferred base address every time. The long term and most suitable solution is to have “relative offsets”, where you use relative offsets to the function address instead of using absolute addresses. The preferred way is to get a function pointer in a loaded DLL is to call GetProcAddress Function. GetProcAddress( ) gives you the address of an exported symbol from a loaded DLL. To get the base address of a loaded DLL, you can use EnumProcessModulesEx Function and then for each, call GetModuleInformation Function .
-Sandeep Sharma
Disable Aslr Windows 10 Free
Windows SDK